Prey is an application that can track your computer should it get stolen or lost. The program is free (with pro accounts available). It is released under the CC-BY-SA licence.
The giveaway info is located at the end of this post.
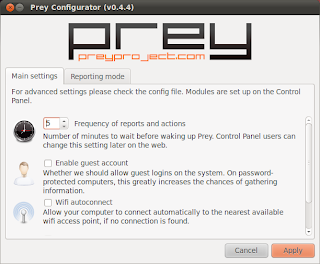
Once you have installed Prey, you must configure it. To do this run the configuration wizard in Applications + System Tools + Prey Configurator. You must enter the root password to configure Prey. When you open it you will see two tabs. The first is labeled Main Settings. Under this tab you can choose options such as how often a report is sent, enabling a guest account and WiFi auto connect (to connect to open WiFi networks automatically).
The second tab, labeled Reporting Mode, lets you choose whether or use Prey’s on-line control panel or the standalone version. I will be demonstrating the control panel method. Select Prey + Control Panel (Recommended) and click forward.
If you have an account click existing user and enter you email and password. If you don’t have an account, select New user and click forward.
Enter you name, email address and password and click apply.
After creating your account you must verify you account. You will receive and email similar to the following. Click on the link in the email to verify you account.
After you have activate your account you can log into the control panel. When you log in you will see the computer you added in a previous step.
If you click on that computer you will see details about that computer. This included the name, type, OS, etc. This is also the screen that is used to mark the computer as missing.
If you click on Modules in the top navigation panel, you have access to various part of Prey. Two types of modules are available: Report and Action modules. Report modules run when the computer is marked as missing. The Network modules gives will tell you about the Internet connection. The Session module will return a screenshot, modified files and running programs. The Web cam module will take a picture using the internal camera. I was not able to test this module as my camera is broken. The last report module available is Geo; this module will find you computer and put the location on a map. Action modules are run as soon as Prey receives the command (this requires version 0.4 or higher). The action modules that are included are Alarm, Alert, Lock and Secure. These modules play a loud sound, send the user a message, lock the computer and deletes personal date, respectively.
This stuff is all useful, but now I will show you what happens when you lose your computer. When you lose you computer, you should log into Prey and mark you device as missing.
Now you wait. When Prey receives a report, you will receive and email similar to the email below.
Click on the link to the report. When you open the report you will see info about the location of your computer. My report shows the uptime (the amount of time the computer has been on), user(s) currently logged in, active connections and WiFi info. It also includes a screenshot and a map. The map shows where the computer is. It uses WiFi and or GPS to find the location of the computer. The location I given was very accurate; less than 100 meters off. This is what my report looked like.
As afore define:mentioned, Pro accounts are available, These plans allow for more computers, active mode (report the last time computer checked in), automated deployment, SSL encryption and two minute report intervals.
I will be giving away five of the Micro plans. These plans give you all of the features mentioned and a maximum of five devices. All you need to do to be entered is enter your name and email address here. The contest will close on next Friday on October 15. I will announce the winners on October 18.
The giveaway info is located at the end of this post.
Once you have installed Prey, you must configure it. To do this run the configuration wizard in Applications + System Tools + Prey Configurator. You must enter the root password to configure Prey. When you open it you will see two tabs. The first is labeled Main Settings. Under this tab you can choose options such as how often a report is sent, enabling a guest account and WiFi auto connect (to connect to open WiFi networks automatically).
The second tab, labeled Reporting Mode, lets you choose whether or use Prey’s on-line control panel or the standalone version. I will be demonstrating the control panel method. Select Prey + Control Panel (Recommended) and click forward.
If you have an account click existing user and enter you email and password. If you don’t have an account, select New user and click forward.
Enter you name, email address and password and click apply.
After creating your account you must verify you account. You will receive and email similar to the following. Click on the link in the email to verify you account.
After you have activate your account you can log into the control panel. When you log in you will see the computer you added in a previous step.
If you click on that computer you will see details about that computer. This included the name, type, OS, etc. This is also the screen that is used to mark the computer as missing.
If you click on Modules in the top navigation panel, you have access to various part of Prey. Two types of modules are available: Report and Action modules. Report modules run when the computer is marked as missing. The Network modules gives will tell you about the Internet connection. The Session module will return a screenshot, modified files and running programs. The Web cam module will take a picture using the internal camera. I was not able to test this module as my camera is broken. The last report module available is Geo; this module will find you computer and put the location on a map. Action modules are run as soon as Prey receives the command (this requires version 0.4 or higher). The action modules that are included are Alarm, Alert, Lock and Secure. These modules play a loud sound, send the user a message, lock the computer and deletes personal date, respectively.
 |
| Click on the image for a larger view. |
This stuff is all useful, but now I will show you what happens when you lose your computer. When you lose you computer, you should log into Prey and mark you device as missing.
Now you wait. When Prey receives a report, you will receive and email similar to the email below.
Click on the link to the report. When you open the report you will see info about the location of your computer. My report shows the uptime (the amount of time the computer has been on), user(s) currently logged in, active connections and WiFi info. It also includes a screenshot and a map. The map shows where the computer is. It uses WiFi and or GPS to find the location of the computer. The location I given was very accurate; less than 100 meters off. This is what my report looked like.
 |
| Click on the image for a larger view. |
As afore define:mentioned, Pro accounts are available, These plans allow for more computers, active mode (report the last time computer checked in), automated deployment, SSL encryption and two minute report intervals.
I will be giving away five of the Micro plans. These plans give you all of the features mentioned and a maximum of five devices. All you need to do to be entered is enter your name and email address here. The contest will close on next Friday on October 15. I will announce the winners on October 18.
All images here are from Prey's web or desktop interface and gMail.
_006.png)
_007.png)
_008.png)
_009.png)






0 comments:
Post a Comment